Welcome to the second installment in our three-part blog series about enterprise vaults – what they are, the hidden risks they carry, and how you can stay resilient.
In our previous post, we explored why enterprise vaults play a critical role in resilience, how they work, and what to consider when choosing the right one for your organization.
Today, we’ll examine a strategic set of critical weaknesses – including zero-day vault vulnerabilities – that often remain hidden and can affect even the most secure vaults.
No organization can afford to ignore these weaknesses. Because, when a determined, sophisticated threat actor succeeds in exploiting even one, the consequences can be catastrophic.
And because these flaws are so difficult to detect – requiring deep expertise and relentless effort to uncover – it’s essential to recognize that they exist and to understand why they’re so hard to find.
Why enterprise vaults are a high value target
First, it’s important to understand why detecting hidden weaknesses – and protecting the enterprise vault – is so critical.
The enterprise vault sits at the center of your organization’s infrastructure, spanning services, cloud environments, CI/CD pipelines, and more. When compromised, it effectively hands attackers the master key to all the systems your business depends on – profoundly and dramatically amplifying the impact.
And the payout for attackers who gain control of a vault is enormous, enabling them to:
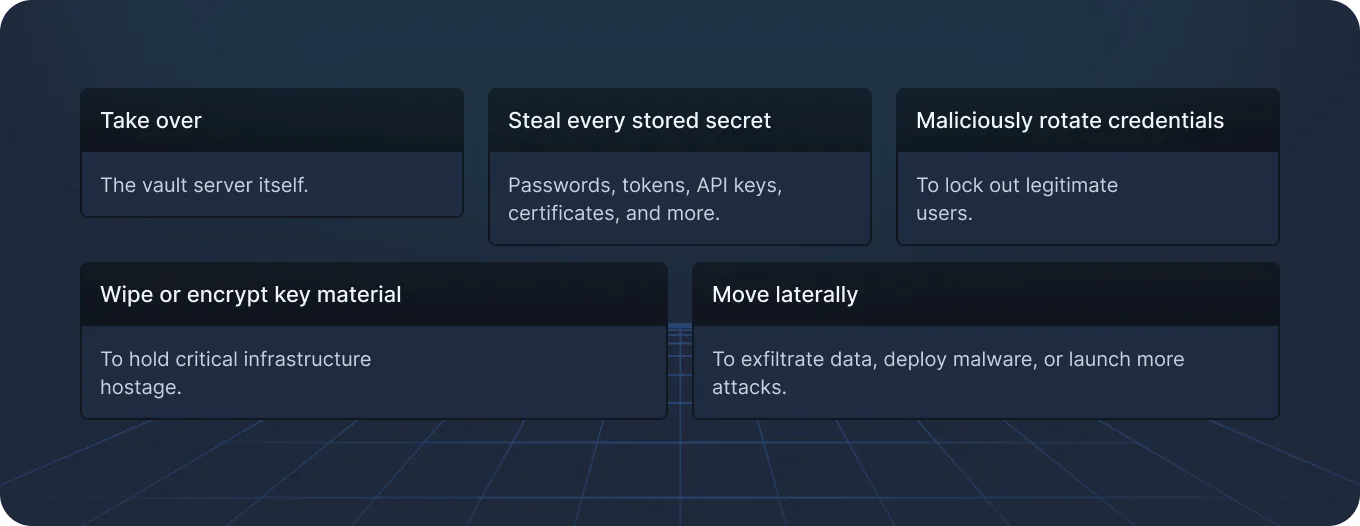
The fallout from such a breach is severe – service disruptions, regulatory penalties, data loss and tampering, reputational damage, and remediation costs that can reach hundreds of thousands of dollars – and more.
5 key hidden weaknesses – and why they’re so hard to find
Even the most secure vaults can be undermined by operational realities – from misconfigurations to overlooked edge cases. These vulnerabilities don’t necessarily stem from flaws in the vault software itself, but from how it’s deployed, integrated, and maintained.
5 key hidden weaknesses
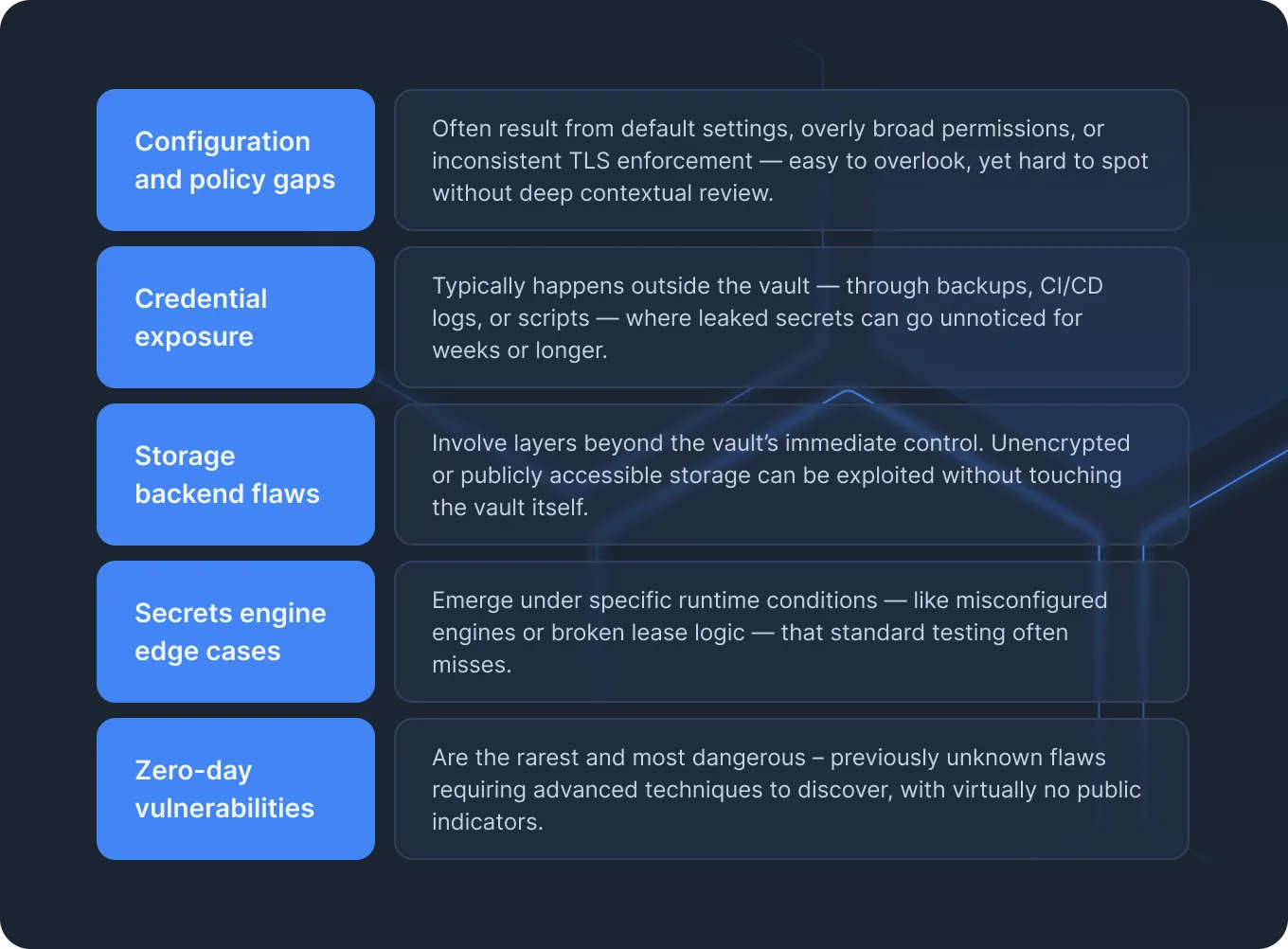
- Configuration and policy gaps
- Misconfigured ACLs (Access Control Lists) or overly broad policies that grant excessive access
- Missing certificate validation or lack of TLS (Transport Layer Security) enforcement, enabling attackers to intercept secrets in transit
- Credential exposure
- Leaked root tokens or master keys from unsecured backup snapshots or CI/CD logs
- API or UI endpoints inadvertently exposed to the internet without proper network restrictions
- Storage backend flaws
- Unencrypted or publicly accessible storage (e.g., disk, object store, or Raft cluster)
- Ransomware-style encryption attacks targeting the storage backend
- Secrets engine edge cases
- Unpatched or misconfigured secrets engines that allow privilege escalation or tampering
- Incomplete lease expiration logic that allows secrets to persist indefinitely
- Zero-day vulnerabilities
- Previously undiscovered bugs in the vault’s core code or cryptographic modules that typically require extensive, time-consuming reverse-engineering, fuzzing, or protocol analysis to uncover
Why they are so hard to find
Modern vaults are built to lock down every conceivable attack path. But in real-world environments, misconfigurations, version mismatches, and obscure runtime conditions frequently combine in ways that create hidden openings – often without triggering alerts or obvious symptoms.
That’s exactly what makes vault vulnerabilities so difficult to detect – they hide in the operational details, not in the code itself, but in how the vault is configured, integrated, and maintained across your environment.
Each type of weakness creates risk in its own way – and each can silently undermine your defenses without triggering alarms.
Here’s how they can surface in practice:
In short, vault weaknesses don’t announce themselves – they lurk in infrastructure blind spots, making proactive detection a constant challenge.
The messy aftermath for security teams
When a vulnerability is exploited and a threat becomes real, the vault is compromised – and this isn’t just a high-risk incident, it’s a full-scale security emergency.
Unlike a single exposed secret, a vault breach puts every credential it stores at risk. That means all passwords, tokens, API keys, certificates, and access policies across the entire organization may be exposed or manipulated.
In this scenario, the organization must immediately assume that all secrets are compromised and take urgent action to contain the damage, restore trust boundaries, and prevent cascading failures.
And the burden on the security team is huge, forcing them to execute:
- Mass secret rotation across systems:
all secrets stored in the vault, including API keys, passwords, tokens, and certificates must be considered compromised and rotated immediately. - Revocation of vault access tokens and credentials:
all vault-issued tokens, session credentials, and certificates must be revoked to eliminate unauthorized access paths. - Full vault configuration and policy audit:
access control policies, authentication methods, and secret engine configurations must be audited for weaknesses or misconfigurations. - Comprehensive forensic investigation:
the attack vector, timeline, accessed secrets, compromised tokens, and any misuse thereof must be identified. - Extensive mitigation and handling of reputational damage:
management, corporate, marketing, and customer-facing teams must work in coordination to reassure customers, partners, prospects, and investors – and restore confidence in the organization’s security posture. - Regulatory and stakeholder disclosure:
if customer or regulated data is affected, the incident may trigger mandatory disclosures.
Each task is resource intensive, disruptive, and costly, which is why preventing that initial foothold is so critical.
So, what can you do to stay protected?
Protecting your vault goes beyond strong policies, encryption, and perimeter controls. It requires proactively identifying misconfigurations, edge cases, and operational blind spots – before attackers do.
In our next and final post, we’ll share proven strategies for vault defense and risk mitigation. Stay tuned.
In the meantime, to learn more about how you can determine how secure your enterprise vault really is, we invite you to speak with an expert by reaching out to us at hello@cyata.ai.
The Control Plane for Agentic Identity




