Imagine coming into the office one day to find that a developer has accidentally leaked an API key to a public repository – leaving your sensitive systems, customer data, and critical operations exposed to cyberattacks.
The risk is enormous because API keys, along with passwords and other credentials – known as “secrets” – act as the digital keys to your kingdom. And when they’re compromised, the damage can be widespread and crippling.
Understanding the vulnerability of secrets and the systems designed to protect them – ״enterprise vaults״ – is essential for every security team. That’s why we’re dedicating our latest blog series to vaults, the hidden risks they carry, and what you can do to protect your organization against the danger.
In this first of three blog posts, we’ll dive into what enterprise vaults are, how they work, and what to look for when choosing the right one for your organization.
What exactly is an enterprise vault?
Organizations have dozens to hundreds of thousands of users – human, non-human, and agentic identities – each requiring access to data, systems, applications, and services.
To authenticate, authorize, and secure this access, they use secrets, such as:

Since secrets unlock access to your sensitive systems, data, and services, they are the key to your crown jewels. And when an attacker succeeds in compromising a secret, the fallout can be devastating, including, among others, data breaches, data theft, service disruptions, regulatory penalties, reputational damage, and financial loss.
This makes protecting secrets a top priority for CISOs and their teams – but it’s a mission riddled with obstacles that are often difficult to overcome, because:
- Secrets are scattered across pipelines, services, and environments, making it hard for teams to maintain centralized control and contain risk.
- Stringent compliance requirements demand audit logs that are hard to produce, retention policies that often slip through the cracks, and tight controls that can be tough to demonstrate.
- Fast-moving DevOps and automation require dynamic, real-time provisioning, rotation, and revocation of credentials – but doing this manually can break workflows or slow down deployments.
- Hybrid and multi-cloud environments introduce inconsistent tooling and fragmented secret storage across platforms.
- As organizations add more tenants, users, and secrets, the task of managing permissions and ensuring continuous service reliability grows exponentially more complex.
- The proliferation of AI agents – whether operating as assistants or autonomously – introduces a whole new class of identities, making it even harder to track who (or what) has access to which secrets and to ensure accountability.
This is where a secrets management program – with an enterprise vault at its core – comes into play.
Secrets management & the enterprise vault: your first line of defense
To overcome the challenges of securely handling, storing, and transmitting secrets, many organizations today turn to secrets management – with the enterprise vault at its core.
Under the hood: how vaults work
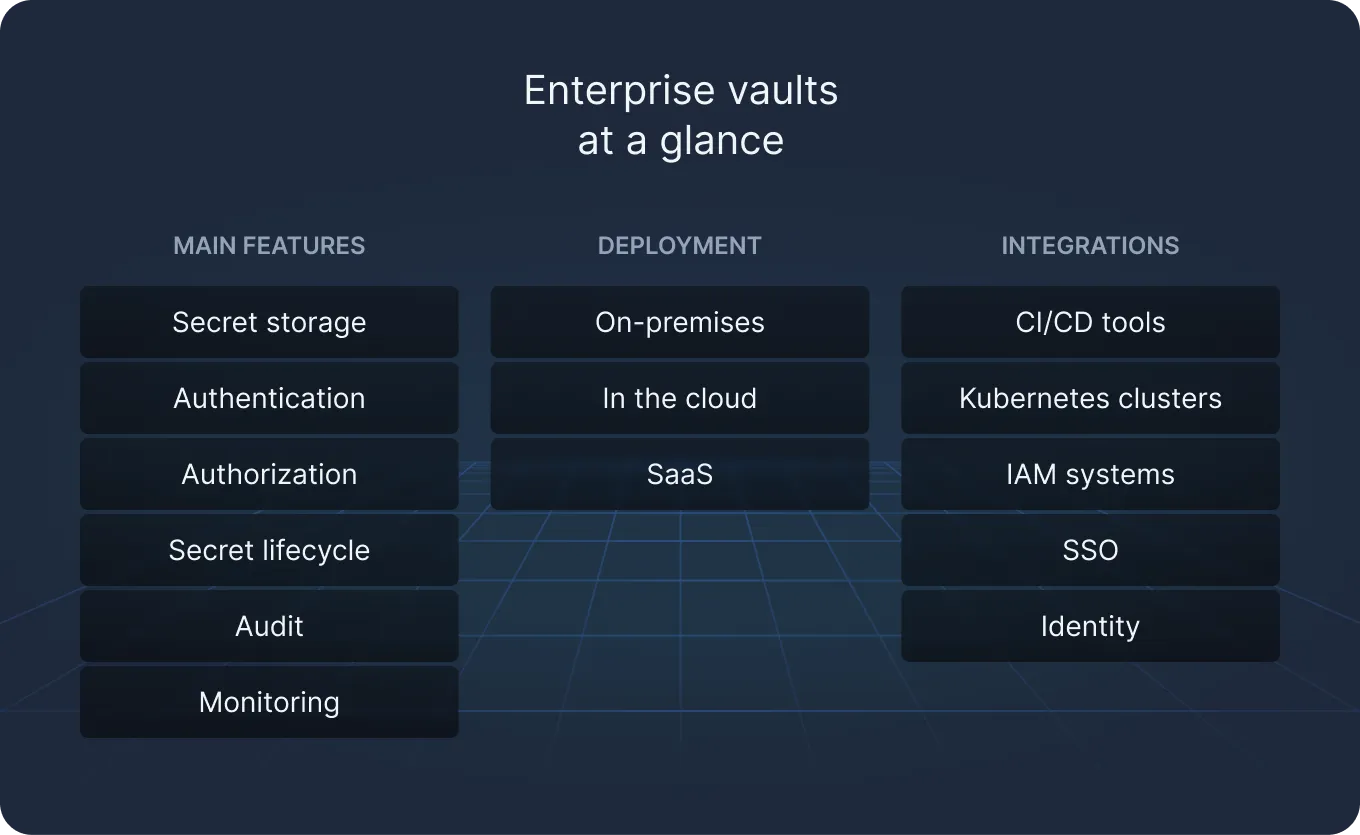
The enterprise vault is your digital fortress. It is an encrypted repository that consolidates all secrets behind reinforced walls, granting access only to those with the right keys.
Authentication and authorization policies govern access. Teams use methods such as AppRole (Application Role) or JWT (JSON Web Token) for machines and LDAP (Lightweight Directory Access Protocol) or SSO (Single Sign-On) for users, enforcing access through role-based or attribute-based policies.
The vault manages the secret lifecycle automatically – it regularly generates, rotates, and updates secrets; revokes access when roles change or risks arise; and leases secrets with automatic expiration. This reduces the attack surface and eliminates the need for hardcoded, long-lived credentials
It logs every access request for auditing and monitoring, recording the user identity, timestamp, method, and outcome.
And when integrated with SIEMs and alerting systems, it enhances visibility, supports compliance, and helps in optimizing threat detection.
Enterprise vaults can be deployed on-premises, in the cloud, or as a SaaS solution. Storage can be segmented by roles, namespaces, or application, and they typically integrate with CI/CD tools (e.g., GitHub Actions, Jenkins), Kubernetes clusters (via CSI drivers or sidecars), cloud IAM systems, SSO, and other identity providers.
Which enterprise vault is right for you?
Organizations can choose from a range of open-source, commercial, and cloud-native secrets management solutions, each with different strengths depending on their infrastructure, scale, and security requirements.
Solution types include enterprise-wide secrets vaults, DevOps-centric managers, and offerings from cloud providers or privileged access management (PAM) vendors.
Enterprise-wide
- Secrets management and cryptographic engine designed for dynamic, multi-cloud and hybrid environments
- Centralized secrets storage with access via API
- Dynamic credential provisioning with automatic expiration
- Identity-based access controls supporting human and machine authentication
- Encryption as a service for data at rest and in transit
- Certificate management for generating, rotating, and revoking certificates
- Distribution, enabling, disabling, and rotating encryption keys
DevOps focus
- Designed to secure secrets across DevOps pipelines and CI/CD environments
- Provides centralized secrets management with encryption
- Offers role-based access control (RBAC) for securing machine and application identities
- Integrates with container orchestration platforms and developer tools, e.g., Kubernetes, Jenkins, and Ansible
- Open source and commercial options
Cloud providers
- Managed secrets management services
- Storage of secrets within each cloud environment
- Native identity and access integrations (IAM-based)
- Automatic rotation and audit logging
- Ideal for organizations that are heavily invested in a single cloud provider and want low-friction integrations
- Broader privileged access management (PAM) solutions that include integrated secrets management
- Vaulting of privileged credentials
- Access controls for high-risk users
- Audit logging for compliance
Next up: how secure is your vault?
Enterprise vaults today are an essential line of defense for protecting the secrets that keep your business running. But even the strongest fortress has hidden cracks.
Stay tuned for part two of our blog series, where we’ll uncover the common risks that can hide in enterprise vaults – often remaining unknown and undetected until substantial damage is done.
In the meantime, to learn more about how you can stay safe, we invite you to speak with an expert by reaching out to us at hello@cyata.ai.
The Control Plane for Agentic Identity






