On August 8, 2025, a threat actor used stolen OAuth tokens from the Salesloft Drift app to log into hundreds of customer Salesforce tenants and pull data at scale. Google’s Threat Intelligence Group tracked the activity through at least August 18, and later confirmed the actor also abused OAuth for the “Drift Email” integration to access a very small number of Google Workspace mailboxes that had explicitly connected Drift. Salesforce removed the Drift app from AppExchange and revoked tokens, and Google disabled the Drift Email integration and revoked the related tokens.
Cloudflare’s public write up shows what this looked like in practice. The actor enumerated objects, measured tenant size with SELECT COUNT() calls, and then pulled case text using the Salesforce Bulk API 2.0. Finally they deleted the Bulk job to hide the trail. Cloudflare rotated 104 internal API tokens found in the exfiltrated case text and notified customers.
Multiple outlets now put the potential victim count in the high hundreds. Zscaler and Palo Alto Networks disclosed exposure of Salesforce case and contact data, and Salesforce said the issue was limited to the Drift connection, not a vulnerability in Salesforce itself.
What actually failed
This was not an endpoint or network failure. It was an agentic identity failure.
OAuth bearer and refresh tokens minted for a trusted agent were stolen and reused from attacker infrastructure. Long lived or refreshable tokens with broad scopes mirrored the app’s access in each tenant. Since activity came from a known connected app, most monitoring did not ring any bells. GTIG’s guidance and Cloudflare’s timeline both show the same pattern: normal looking API traffic, large SOQL pulls, Bulk API jobs, and a tidy clean up step. Logs survived. Detection did not.
Key lesson
The biggest breaches in 2025 are not riding malware. They are riding our agentic identity blind spots. We trust integrations like employees, but we rarely govern, monitor, or offboard them like employees.
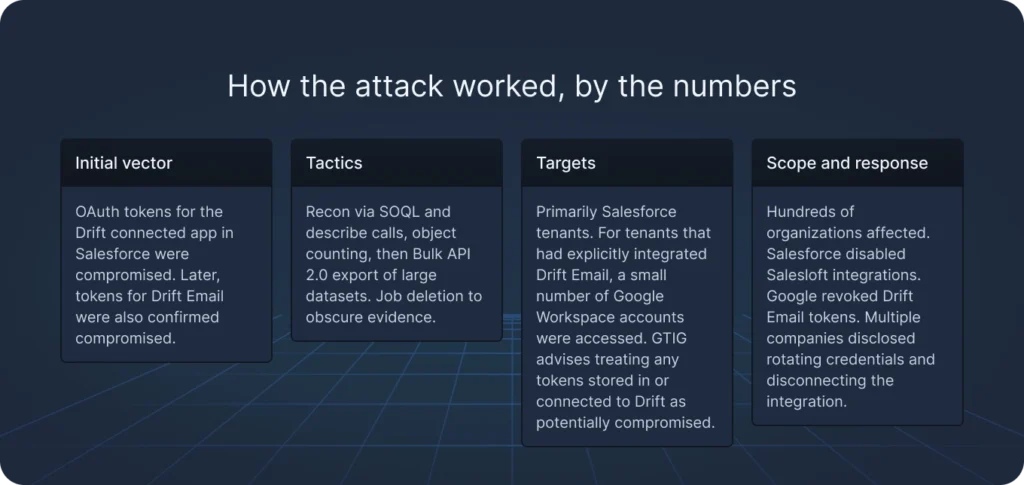
How the attack worked, by the numbers
- Initial vector: OAuth tokens for the Drift connected app in Salesforce were compromised. Later, tokens for Drift Email were also confirmed compromised.
- Tactics: Recon via SOQL and describe calls, object counting, then Bulk API 2.0 export of large datasets. Job deletion to obscure evidence.
- Targets: Primarily Salesforce tenants. For tenants that had explicitly integrated Drift Email, a small number of Google Workspace accounts were accessed. GTIG advises treating any tokens stored in or connected to Drift as potentially compromised.
- Scope and response: Hundreds of organizations affected. Salesforce disabled Salesloft integrations. Google revoked Drift Email tokens. Multiple companies disclosed rotating credentials and disconnecting the integration.
Why it was hard to spot
Bearer semantics
A valid access token is a get in free pass until it expires or is revoked. With a refresh token, the party continues. If an attacker uses the same scopes the app already had, controls keyed to user logins and MFA never trigger.
Known app trust
Many orgs implicitly trust the connected app identity. If you do not baseline that app’s normal API patterns, unusual use can hide inside the noise of normal use.
Fragmented telemetry
Token issuance sits at the OAuth server. Data access sits in each SaaS. Without correlation across issuance, validation, and data access, you will not see impossible travel or sudden burst patterns until after exfiltration. GTIG calls out this gap explicitly and recommends correlating Drift connected app events with Event Monitoring and UniqueQuery logs.
A practical detection playbook you can run today
Below are concrete signals mapped to where you can see them. Think small, composable rules that you correlate.
At the OAuth server
- Unusual token issuance for the Drift connected app
- Same client issuing from distant geos within minutes. Excessive token grants. Unexpected or oversized scopes.
- Where: IdP and OAuth server audit logs, Salesforce Connected App audit, Google Workspace token logs.
Between client and resource
- Impossible travel and IP drift
- Token issued in New York, first used from Beijing 5 minutes later. First use from Tor or new cloud IPs.
- Where: IdP sign in logs, resource API access logs. GTIG IOCs include specific IPs and user agents.
At Salesforce
- Unusual SOQL patterns
Bursts of SELECT COUNT() across Account, Contact, User, Case. Repeated describe calls. Sudden growth in UniqueQuery events tied to the Drift connection user. - Bulk API 2.0 spike
Short lived jobs that export large objects followed by job deletion.
Where: Event Monitoring, EventLogFile for API, BULK_API, and URI events. Cloudflare’s timeline shows the exact sequence.
At Google Workspace for tenants with Drift Email
- New token use for Drift Email
- First time token validation from a new ASN or region. Sensitive Gmail read events tied to the Drift Email OAuth client.
- Where: Workspace Admin logs and token audit.
Example starting points
- Salesforce SOQL to enumerate logs
Search EventLogFile for EventType IN (‘API’, ‘BulkApi’, ‘Uri’, ‘UniqueQuery’) where USER_ID equals the Drift connection user, and filter on ClientIp in GTIG IOCs or new ASNs. - Look for deleted Bulk jobs
If you have Bulk API logs in your SIEM, alert on operation = query followed by delete job within minutes for the same jobId. - Geo drift correlation
Join token issuance records with first API use per token. Flag distance over 2,000 km within 15 minutes as an investigation signal.
Immediate containment, in order of operations
Revoke
Revoke Drift connected app tokens in Salesforce and any other platforms that integrated with Drift. For tenants that used Drift Email, ensure Workspace tokens are revoked.
Rotate
Rotate any keys, passwords, or tokens found in Salesforce free text fields and support cases. Cloudflare found 104 of their own API tokens in case text and rotated all of them. Your tenant likely has similar exposure in case bodies and notes.
Hunt
Query Event Monitoring and UniqueQuery logs for the sequences GTIG and Cloudflare published. Review API clients and user agents listed in the IOCs. Use Tor exit node lists as a coarse filter, but do not rely on them alone.
Scope reduction
Audit the Drift connected app or any equivalent agent. Remove full access, enforce IP restrictions on the connected app, and set shorter session lifetimes.
Treat agents as first class identities
Agents look like employees in how they operate. They authenticate, make API calls, process sensitive data, and can trigger automations across SaaS and cloud. They are not managed like employees.
- Inventory each agent identity, the platforms it touches, and who owns it.
- Least privilege by design. Scopes per platform, not blanket full.
- Token hygiene with enforced rotation and short lifetimes. Treat refresh tokens as critical secrets.
- Correlation across issuance, validation, and data access. Put the token lifecycle on one timeline.
- Offboarding that actually revokes tokens in every platform, not just the source app.
Where Cyata fits
Cyata’s thesis has been simple: agents are identities. If you cannot discover them, explain their behavior, and control their access across systems, you will miss the next Drift.

- Discover all agentic identities across IdPs, SaaS, cloud, and developer tooling. See scopes, tokens, and where those tokens are actually used.
- Explain behavior with cross system observability. We baseline each agent’s normal token issuance, validation, and API patterns, then surface geo drift, burst patterns, and Bulk like exfil.
- Control access through policies that enforce scoped permissions, token rotation, IP restrictions, and real time interlocks when an agent’s behavior deviates.
If you are investigating this incident, start with GTIG’s advisory and your Event Monitoring logs. If you are preparing for the next one, make your agents first class identities now.
Sources to start from
Google Threat Intelligence on Drift tokens, scope, IOCs, and Workspace Drift Email actions.
Cloudflare incident timeline showing SOQL patterns, Bulk API exfiltration, and job deletion.
Zscaler and Palo Alto Networks disclosures on impacted Salesforce data.
Salesloft’s own Trust Portal with updates of their investigation.





